Blockchain Security: Protecting Smart Contracts and Crypto Assets
When working with Blockchain Security, the practice of safeguarding blockchain networks, smart contracts, and related assets from attacks, bugs, and fraud. Also known as crypto security, it helps developers, investors, and enterprises keep digital money safe while preserving trust in decentralized systems. Have you ever wondered why a $50 million rug‑pull can still happen after a code review? The answer is that security isn’t a one‑off checklist; it’s a continuous process that blends code analysis, threat modeling, and real‑world testing. In 2025, the market is buzzing with new audit platforms, AI‑driven scanners, and cross‑chain testing suites, all aiming to close the gaps that traditional static analysis missed. Understanding the landscape means knowing the core pieces that make up blockchain security – from the people who write the code to the tools that sniff out hidden bugs. Below we’ll break down the main moving parts so you can see where the risk lives and how to manage it before a hack hits your wallet.
One of the first pillars of Smart Contract Audit, a systematic review of contract code aimed at finding vulnerabilities, logic errors, and gas inefficiencies is the audit itself. A thorough audit looks at everything from re‑entrancy flaws to improper access controls, and it often ends with a public report that scores risk on a scale you can actually understand. Most projects treat this step as a prerequisite because Blockchain Security encompasses smart contract audits – without a solid audit, the rest of your defenses are built on shaky ground. In practice, you’ll see three typical tiers: a basic token review that might cost a few thousand dollars, a mid‑level DeFi protocol audit that runs into the low‑five‑figures, and an enterprise‑grade, multi‑chain audit that can top six figures. The pricing model is usually a mix of fixed fees plus a variable component based on lines of code, complexity, and the expected effort of manual testing.
Another key player in the space is DeFi Security, the set of practices, tools, and standards designed to protect decentralized finance applications from exploits and market manipulation. DeFi platforms often handle large pools of liquidity, so a single bug can cascade into massive losses across the ecosystem. Because of that, DeFi security influences blockchain security costs – a protocol with high TVL will usually face stricter audit requirements and higher fees. Common tools include automated fuzzers, formal verification engines, and runtime monitoring solutions that alert you when a contract behaves outside its expected parameters. Many auditors also run live testnet attacks to see how the system reacts under pressure. This hands‑on approach helps uncover issues that static analysis alone can’t catch, like price‑oracle manipulation or flash‑loan attacks that only surface in real market conditions.
Finally, let’s talk about Blockchain Audit Fees, the cost structure that covers labor, tooling, reporting, and post‑audit support for blockchain security assessments. Understanding these fees is crucial for budgeting, especially if you’re a startup trying to allocate runway. Typical fee components include a base price for code review, a premium for multi‑chain support, and optional add‑ons like post‑audit monitoring or a bounty program to incentivize external researchers. Hidden costs can pop up in the form of revision rounds—most audits include at least two cycles of feedback, but deeper changes can drive the price up quickly. A practical checklist to keep fees in check is to get clear scope definitions, request a detailed breakdown before signing, and ask for a flat‑rate option if you expect many iteration cycles. By mastering the fee landscape, you can avoid nasty surprises and ensure your security investment actually protects the value you’ve built.
Below you’ll find a curated collection of articles that dig into each of these topics in depth. From a 2025 breakdown of audit pricing to a step‑by‑step budgeting guide, we’ve gathered the insights you need to make informed decisions about protecting your blockchain projects. Ready to see how the numbers stack up and what you should look for in a reputable audit partner? Keep scrolling to explore the full set of resources we’ve assembled just for you.
NFT anti-counterfeiting uses blockchain to create unbreakable product authentication. Learn how luxury brands and pharma companies fight counterfeits with digital certificates, why physical security layers are essential, and how businesses can implement it in 2026.
Multisig wallets require multiple signatures to move crypto, making them far safer than single-key wallets. Learn the best platforms like Safe Wallet and Blue Wallet Vault, how they work, and why they're essential for holding large amounts of crypto securely.
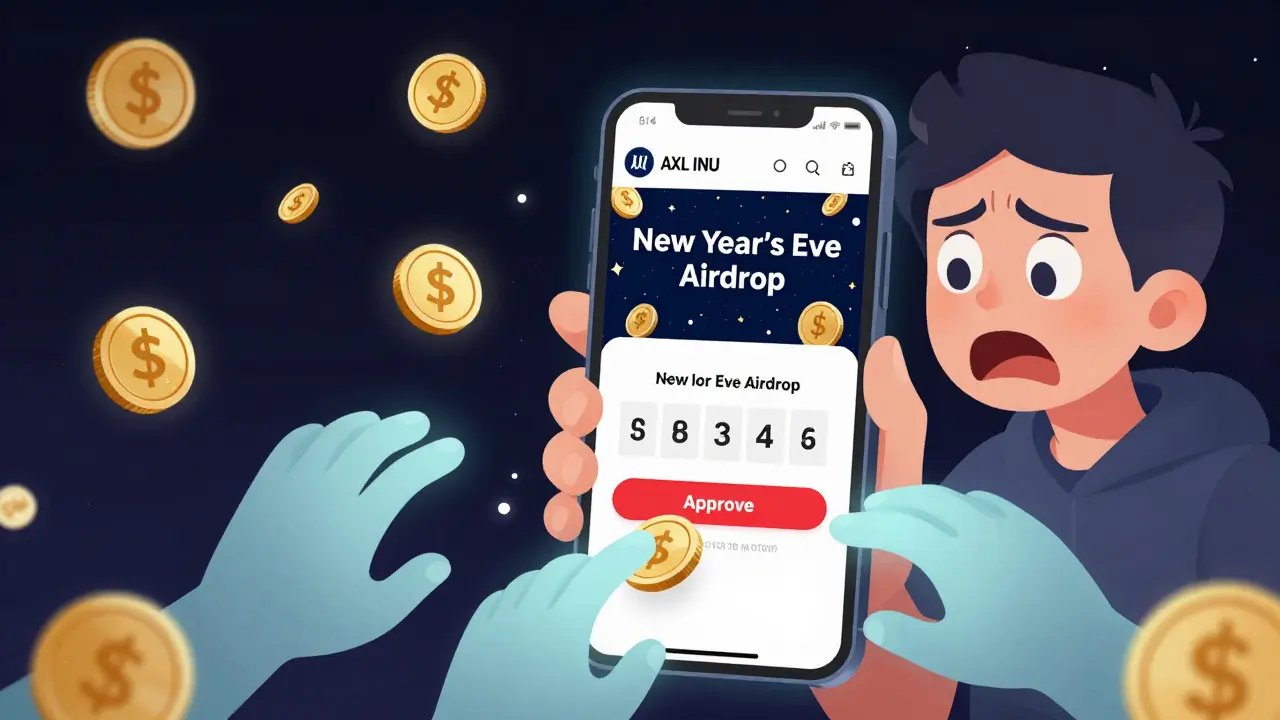
The so-called AXL INU New Year's Eve airdrop is a phishing scam targeting crypto users with fake claims of free tokens. Learn how the scam works, how to spot it, and how to protect your wallet.
Learn how to spot memecoin pump and dump schemes before you lose money. Discover the red flags, real patterns, and proven ways to avoid becoming a victim of crypto scams.
Content monetization smart contracts let creators earn directly from fans using blockchain-no platforms, no delays. Learn how micropayments, subscriptions, and tokenized royalties work today.
DePIN projects use blockchain to turn everyday hardware into shared infrastructure-like Wi-Fi hotspots and solar grids-that anyone can join and earn from. No corporations, no middlemen, just crypto rewards for real-world contributions.
Future Sybil attack prevention methods combine AI, zero-knowledge proofs, and decentralized identity to stop fake accounts without sacrificing privacy. Learn how projects like Formo and Worldcoin are reshaping blockchain security in 2026.
ECDSA, EdDSA, Schnorr, and BLS are the core digital signature algorithms powering blockchain security. Learn how each works, where they're used, and why the future of crypto depends on upgrading them.
KYC in crypto is no longer optional - it's mandatory infrastructure. By 2025, 92% of exchanges enforce identity verification. Learn how AI, regulation, and privacy tech are reshaping crypto compliance - and what it means for users and platforms.
Crypto exchanges use KYC checks, AI-driven transaction monitoring, and global compliance tools to stop money laundering. Learn how real systems work, why they matter, and what happens when they fail.
Public blockchains offer transparency and decentralization but struggle with speed, cost, and privacy. Bitcoin and Ethereum show both the power and limits of permissionless ledgers.
State channels let you make instant, low-cost transactions off the main blockchain by locking funds in a smart contract and settling only the final state. Used in Lightning Network and Raiden, they solve blockchain scaling for frequent, small payments.